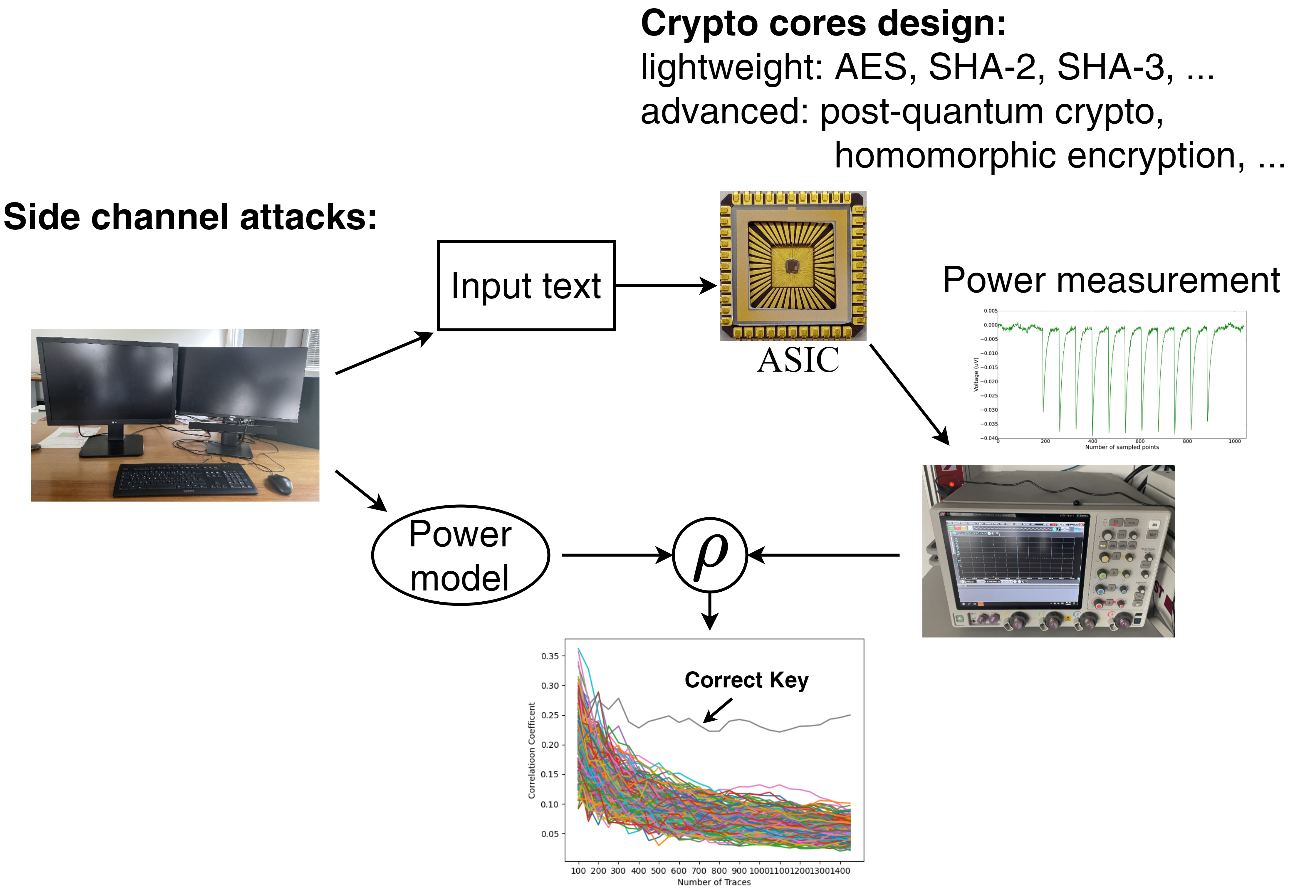
Security has become even more important with the ubiquitous access to internet and intranet of all devices of daily live increasing the attacking surface. In order to address the security challenges, we are developing various cryptographic accelerators covering diverse cryptographic algorithms from lightweight to advanced. The involved computations include FFT, polynomial multiplication, random generation, finite-field arithmetic, etc. The designed cryptographic accelerators are designed to push PPA (performance, power, area) metric while assuring secure and reliable operation with application in IoT, post-quantum security, or for example secure cloud-computing. Furthermore, we are working on various levels to resist the SCA from algorithm to physical design, since physical attack like power side channel attack (SCA) is a big challenge for secure computing. Finally, hardware Trojan is also part of this research field looking into ways to leak information without being noticed – at the end, to design countermeasures protecting the system against these kinds of attacks.
[S. Zhang et al., “A Compact 1,257-Gbps/W Byte-Serial AES Accelerator for IoT Applications in 22 nm", A-SSCC, 2023]
[S. Zhang et al., “A 22-nm 1,287-MOPS/W Structured Data-Path Array for Binary Ring-LWE PQC,” ESSCIRC, 2023]
[C. Lanius et al., “Hardware Trojans in fdSOI,” ISLPED, 2023]
[D. Fallnich et al., “Efficient ASIC Architectures for Low Latency Niederreiter Decryption,” Cryptology ePrint Archive, 2022, eprint.iacr.org]